Read Radius Logs With PowerShell
Reading Time: 2 minutesRecently, I have been troubleshooting radius. Radius hasn’t changed in decades. I say this lightingly too. The network policy server is a feature that helps with connecting things like unifi wifi and more. Each radius connection produces a reason code. Today we want to look through the radius logs and get as much useful information without screaming at the screen. Radius logs are a little daunting. This is why many people use an SQL server for the radius logs. However, if you are not one of those people who can do this, the traditional radius logging works wonders. So, we will read radius logs with PowerShell.
Radius Logging
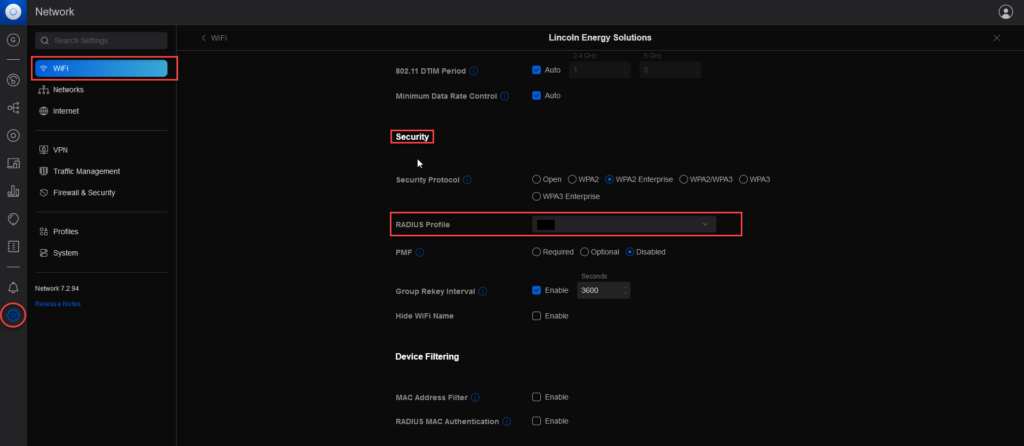
Before we start, we need to know what we are dealing with. The standard location for readius logs is: C:\Windows\System32\LogFiles. You can change this location as you see fit. I personally changed my locations to a c:\logs\radius location. This helps me find it quicker and generally, I don’t have trouble guessing what is what. You can set the radius log location by doing the following:
- Start Network Policy Server
- Click account
- Under Log File Properties click Change Log File Properties
- A box will pop up called “Log File Properties” Click on the “Log File” tab.
- This is where you can change your directory.
- Change your Format to DTS Compliant. As this script works best with it.
- I personally like smaller files when I am working with log searches. So I select the “When log file reaches this size:” I select 1 – 5 MB.
- Click ok
Now your log files will live wherever you told them. You will need to change the script around a little if you are using a different location than me.
The Script and Breakdown
$NPSLogs = Get-content -Path "C:\Logs\Radius\IN2308.log" | Select-Object -Last 6
foreach ($NPSLog in $NPSLogs) {
[pscustomobject][ordered]@{
TimeStamp = ([xml]$NPSLog).event.Timestamp.'#text'
ComputerName = ([xml]$NPSLog).event.'Computer-Name'.'#text'
Sources = ([xml]$NPSLog).event.'Event-Source'.'#text'
Username = ([xml]$NPSLog).event.'User-Name'.'#text'
CalledStationId = ([xml]$NPSLog).event.'Called-Station-Id'.'#text'
CallingStationId = ([xml]$NPSLog).event.'Calling-Station-Id'.'#text'
NasPortType = ([xml]$NPSLog).event.'NAS-Port-Type'.'#text'
NasIdentifier = ([xml]$NPSLog).event.'NAS-Identifier'.'#text'
NasPort = ([xml]$NPSLog).event.'NAS-Port'.'#text'
ClientIPAddress = ([xml]$NPSLog).event.'Client-IP-Address'.'#text'
ClientVendor = ([xml]$NPSLog).event.'Client-Vendor'.'#text'
ClientFriendlyName = ([xml]$NPSLog).event.'Client-Friendly-Name'.'#text'
ProxyPolicyName = ([xml]$NPSLog).event.'Proxy-Policy-Name'.'#text'
ProviderType = ([xml]$NPSLog).event.'Provider-Type'.'#text'
SamAccountName = ([xml]$NPSLog).event.'SAM-Account-Name'.'#text'
FQUsername = ([xml]$NPSLog).event.'Fully-Qualifed-User-Name'.'#text'
AuthType = ([xml]$NPSLog).event.'Authentication-Type'.'#text'
Class = ([xml]$NPSLog).event.Class.'#text'
PacketType = ([xml]$NPSLog).event.'Packet-Type'.'#text'
ReasonCode = ([xml]$NPSLog).event.'Reason-Code'.'#text'
TunnelClientEndpt = ([xml]$NPSLog).event.'Tunnel-Client-Endpt'.'#text'
}
}
As you can tell, this script needs to be used on the server in question. However, You could wrap this script into a nice wrapper. That would allow you to execute on remote machines. The breakdown is very simple on this one as well. DTS is an XML format. Thus, you just need to use the [XML] before any of the lines. The XML is formatted with the event, it’s name, and the text. It’s a very simple setup. From there I select what I want and give it in a pscustom object. That’s it. Its a very simple setup. That’s why we should always read radius logs with Powershell.