
Group Policy Troubleshooting – Delegation
Reading Time: 4 minutesA while back, a client called and told me he made a few new group policies, and they were not working as expected. He stated some policies applied to the wrong users, while another didn’t apply at all to any users. He stated he set the security group correctly. When I hear, “The policy didn’t apply, or the policy is applying to the wrong person, I immediately think, delegation. Let’s look at the two policies and what broke them.
Scenario – Restricted Google Chrome Policy applying to everyone.
This client had special needs to restrict google chrome. This included items like the auto-fill feature to be turned off, prohibiting Chrome extensions, and more. This was user policy. He only wanted it to Restrict to the techs computers, and not the management nor the IT department.
Who, What, Where, When, How
- Who: This was effecting all the users at once.
- What: A chrome policy that restricted users in google chrome.
- Where: Everywhere
- When: After the client applied the google chrome policy.
- How: Through Group Policy.
It was clear, group policy was the issue. So, I took a gander at the delegation of the policy he called “Restricted Chrome Policy”. The policy
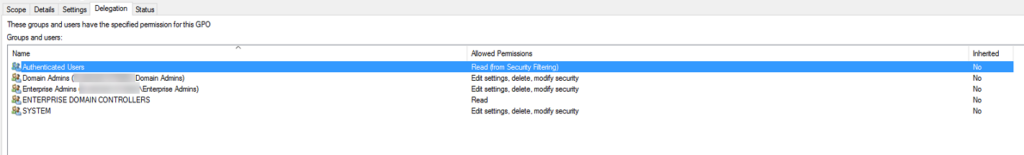
Immediately, I saw that the tech group was not in the policy. In fact, this was the standard policy setup. However, one thing I have learned over the years, never to assume. So, I clicked the authenticated users and clicked the advanced button at the bottom of the delegation screen.
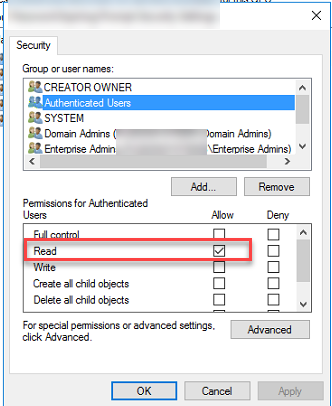
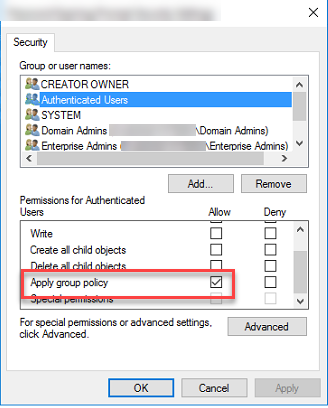
In this case, I was right in my assumption. The authenticated user are every user on the domain. This is a large group and it’s required for any group policy to work. The thing about it though, if the “Apply group policy” is checked, it applies the group policy to everyone. (Unless another policy closing to the ad object applies or enabled that overwrites the policy in question. )
This is what I did. I unchecked the “Apply Group Policy” check box. Created a security group called SG_Policy_Chrome_Tech and added all the techs inside that group. Then I add that group to the delegation. I made sure the read was checked and apply group policy was checked. Then on an end user’s computer, I ran the gpupdate /force and the policy was applied correctly.
Scenario – Group Policy wasn’t applied at all.
The second policy was harder to track down as it was a password alert policy. (Something I will cover later). The policy was to prompt a user within 14 days that their password is going to expire. It is done with a simple logon script. Very simple script, very simple policy. They called it “Password Prompt”. The client discovered it wasn’t being applied when he completed a gpresult /r on an end-user and didn’t see it. It turns out that it was only meant for users and not service accounts.
Who, What, Where, When, How
- Who: Users
- What: Password Prompt is not applying
- Where: Main OU level
- When: Always
- How: Hum…
By default, group policy management opens the policy where you can see the scope. I noticed right there something was missing. The client had set the user’s group “employees” but I didn’t see authenticated users. I went to the delegation tab, and I was right. There was no authenticated users group. I went through and added the authenticated users group, and made sure the “Apply this policy” wasn’t checked, and read was checked.
The reason we do this is we want everyone to read the policy, but not apply it. How can you apply something you know nothing about? The same concept is applied here. The computer account can’t read the policy if it doesn’t know it exists. The authenticated user allows that reading. Once set, and a good old gpupdate /force was applied. The password policy showed applied.
Another way you can go about doing this is by adding the domain computers group. As it is the computer that will need to read the policy. This is thanks to the June 14 2016 security update.
The takeaway
Delegation is important. The Authenticated user’s group is required in all group policies at a minimum of read. If you set the authenticated user’s group to read-only, you use a security group with apply in order to apply a policy. The scope screen only shows you what is being applied, and thus, you may not even notice the authenticated users.
I hope this has been helpful for you. As always, if you have questions reach out to me.
